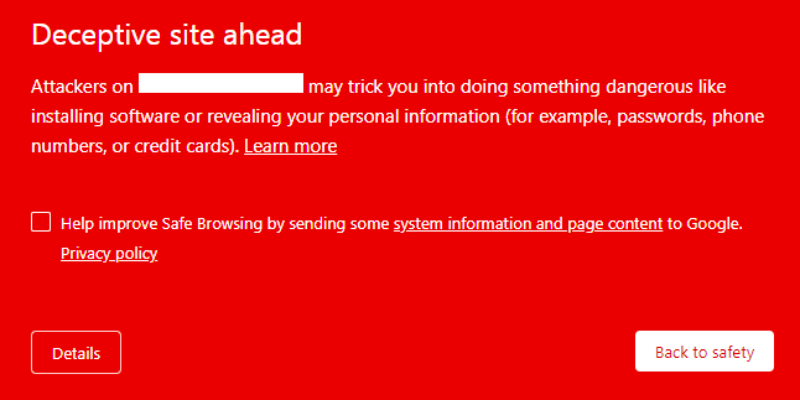
The big red screen appears on your google chrome browser. The warning near your site address bar says ‘Dangerous’. These are the signs of your website being on Google’s blacklist because your site has been hacked and it is deceptive.
The first thing to do is scan your website to be 100% sure of the hack.
The Deceptive website warning is Google’s warning to visitors about your WordPress website, as malware has made your website dangerous for them to visit. It is a serious situation to be in, as malware can cause considerable losses for your website.
We’re going to level with you: having the Deceptive Site Ahead warning appear for your WordPress website is bad. But, it can be fixed. We will show you how to fix the google chrome deceptive site ahead in this article.
What is the Deceptive Site Ahead warning?
The Deceptive Site Ahead warning is quite simply Google telling its visitors that the website they are about to visit is unsafe. It usually means that the website has malware or deceptive content and is being used for phishing attacks. This could lead to visitors being exposed to spam pages, inappropriate or unsafe content, or even be a front for gathering credit card information from them.
It is a Google Safe Browsing warning that appears when visitors click through to a hacked WordPress website from Google chrome search results. It can appear as a big red screen (and is sometimes known as the red screen of death) before someone clicks through to the website, or as a ‘Dangerous’ warning in the address bar.
The deceptive site ahead warning is not restricted to Google, or to Chrome, because every other browser also uses the same blacklist to protect their users. This means that regardless of whether your user is on Internet Explorer, Safari, Firefox, or Opera, they will see some variant of this warning.
If you use Google Search Console for your website, you will also see warnings flagged in the Security Issues tab. Search Console will send you emails to the effect as well, in order for you to address these issues on priority.

Why is the Deceptive website warning appearing on your website?
The Deceptive Site Ahead warning is a sure sign that your WordPress website has been hacked. In fact, in most cases, if a website has been flagged by Google, it has been hacked for some days at the very least.
Additionally, the chrome deceptive Site Ahead warning is only one of Google’s warnings. Your website could contain vulnerabilities in plugins or not adhere to good WordPress security practices, like using HTTP instead of HTTPS. In these cases, Google may flag your site as ‘Not secure’ or ‘This site may harm your computer.

All of this is bad for your website and its SEO rankings. However, it would be much worse if the hack went undetected. We will talk more about the impact of hacks later on in the article. For now, we want to focus on the problem of malware at hand.
How to remove malware infection from your website?
To get rid of the Deceptive Site Ahead warning, you need to remove the malware infection that is causing the warning in the first place. We detail the steps of removing malware below, but let’s look at a quick overview first. This is a 3-step process:
- Scan your website for malware
- Clean the malware from your website
- Remove deceptive site ahead message by submitting review request to google
Important things to remember
Before you get started, there are a few things you need to keep in mind.
- Act fast: Apart from malware wreaking havoc on your website, Google also tracks how long people take to action the security issues on their website. Now is not the time to delay.
- Malware removal is difficult: For most people, in any case. You can disregard our caution if you are a WordPress expert. But we have seen too many broken websites because of botched malware removal attempts to count, and it is awful to have to break the bad news to website admin.
- You also need to fix the underlying issues: Hackers were able to infect your site because of a vulnerability or a backdoor. Although there are other ways they could have gained access to your site, over 90% of hacks occur because of vulnerabilities. If you get rid of the malware, but not the vulnerability, the infection will reoccur.
- There is bad advice out there: A lot of people come to us with broken websites, because of the fixes they have read about online. The bad advice is not deliberately malicious, but it can do more harm than good.
Without further ado, let’s start saving your website from hackers.
1. Scan your website for malware
The first thing you need to do is scan your website for malware. Yes, you know your website is already hacked, but a deep scan will check all the files, folders and database for malware, deceptive content, and vulnerabilities. As we said before, cleaning the malware out isn’t enough; you need to get rid of the underlying problem that allowed it in the first place.
There are a few ways to scan your website, and we will talk a little bit about each method.
- Deep scan your website [RECOMMENDED]: To check every file, folder and entry in the database of your WordPress website, you need to install a WordPress security plugin and run a scan. Deep scans will ferret out every line of malware and every changed variable that is suspicious. Install MalCare, and get scan results in less than 5 minutes.
- Use an online scanner: If you want to scan your website without installing a security plugin, you can use an online scanner like Sucuri Sitecheck. This type of scanner will scan all the publicly visible code of your website. This is a good first step in diagnostics, because a frontend scanner will flag malware in posts and pages.However, it falls short when scanning WordPress core files, like the wp-config file for example. Malware doesn’t always conveniently stick to publicly visible areas of code, so this is a half measure at best.
- Scanning manually: Apart from the obvious reasons of human error, there are many, many reasons why we do not recommend anyone to manually scan (or for that matter clean) their website. With big websites, this is a daunting task and prone to lots of malware escaping unnoticed.
The best way to find malware in your website is to scan it with a security plugin, like MalCare. You will have a conclusive assessment of the infection, and can move ahead with cleaning the malware.
Other diagnostics to check for malware
If you use a security plugin that is not MalCare to scan your website, you may experience false positives. Other plugins like WordFence and iThemes have been known to flag innocuous custom code as malware because of their scanning mechanisms.
Although the Deceptive Site Ahead error message is enough indication of malware, you can use the following methods to test for malware infections yourself.

- Visit your website from an incognito browser or a different computer, as hackers can cloak malware from admin
- Check the number of pages indexed on Google. If spammy pages have been inserted into your website, you will see a number mismatch for search results. For instance, if your website has around 10 pages, you should expect to see a few more or less. An outsized number in say the 100s or even 1000s is a good indicator of spam pages.
- Look for unusual user activity logs, which can indicate a hacker has gained unauthorized access to your website with a user account. t can either be a compromised one, or a ghost user, that shows unusual activity for that account. Changed user permissions, a flurry of changes on posts and pages, or the creation of new pages altogether are good indicators here.
- Check for strange trends in analytics data, like spikes in traffic. If you are running a marketing event or ads then these spikes may be warranted, otherwise they can be symptomatic of malware.Additionally, your website will take a hit in traffic numbers because of the Deceptive Site Ahead warning. Fewer people visiting your website will result in lower numbers, and you will see a corresponding dip in engagement metrics as well.
- Look for Google Search Console warnings. Google tries to warn its users in order to promote a safe browsing experience. Even if you do not have a search console account, you can still check if Google throws up a ‘Not secure’ warning for your website.
- Vulnerability checks for installed plugins and themes, if you haven’t kept them updated. If you have older versions of plugins and themes, there are probably the entry points for the malware. If your dashboard has an ‘Update now’ flag next to an installed plugin or theme, Google for recently discovered vulnerabilities in those particular ones.
- Remove nulled plugins and themes. It is tempting to get a premium plugin or theme for nothing, but there is always a hidden agenda. There is no such thing as a free lunch. Premium plugins and themes have cracked licenses, which means that the original developers will not be able to support it with updates. And that is the benign side of nulled software. This software often has backdoors and malware built into them, so hackers can get to your website when it is installed.
2. Clean malware from your website
Alright, we are now in battle-mode. This is where things can get gnarly, depending on the route you take to remove malware from your website. There are 3 ways to get rid of malware from a WordPress website that is causing deceptive site ahead, and we are going to talk about them each, in order of most effective to least effective:
- Use a security plugin to remove malware
- Hire a security expert to clean your website
- Clean your website manually
The most important thing is to clean your website fast. Every moment you leave the malware on your website, the losses are getting worse. In some cases, they are getting exponentially worse.
Option 1: Use a security plugin to remove malware from your website
We recommend you use MalCare to remove malware from your website. It is the best-in-class security plugin for your WordPress website because it will remove the hacks surgically from your website files and its database. At the end of a MalCare cleanup, you will have your website and data back completely intact.
To use MalCare, all you need to do is:
- Install MalCare on your website
- Scan your website from the dashboard
- Auto-clean when prompted to get rid of the malware

And that’s it. The cleanup takes a few minutes to complete, and your website is as good as new once again. If you used MalCare to scan your website, then all you need to do is upgrade to clean instantly.

Once MalCare is installed, it will scan your website daily for threats, and protect your website from bots and hackers. With MalCare you are gaining a powerful web application firewall as well which will help you filter out malicious traffic from country or device, and a dashboard from which you can administrate your website easily.
How to use MalCare if you don’t have access to your website?
When your website is hacked, it can often feel like every door is slamming shut in your face. Google has flagged your website with the deceptive site ahead, and you now may not have access to your website at all. This state of affairs can happen if the hacker has infected your website with a redirect hack, or a web host has suspended your account. Either way, you cannot access wp-admin to install a security plugin.
All is not lost though. Get in touch with us or drop us an email at support [at] malcare [dot] com, and we will guide you through the next steps. We will walk you through the process of getting your website unsuspended too.
Option 2: Hire a WordPress security expert
If you choose not to install a security plugin, then please go the WordPress security expert route to clean malware and deceptive content from your website. While we cannot speak to the efficacy of other security experts, we expect them to be plugged into the WordPress website security domain and thus be able to provide a viable solution.
Our experience has been that the really effective security experts are prohibitively expensive; justifiably so, as what they do is incredibly technical and difficult. We should know, because we have a team of them at MalCare. The only difference is that our experts’ services are available for free with our security plugin.
Option 3: Clean the website manually
We have cleaned thousands of websites for customers, and even then we don’t recommend manual cleaning. It is a fraught process with a tremendous amount of risk, with low chances of success—unless you are a bonafide WordPress security expert. (In which case, you wouldn’t need to read this article.)
If you are going to tackle the malware on your own steam, we will help you to the best of our ability. We cannot guarantee that you will be successful, because each hack can be very different, and there is no one-size fits all approach.
To begin this process, you need to know the following:
- WordPress file structure and its working: Which files are important, how they work with each other, how themes and plugins are installed, how they work.
- Programming: What do the scripts do? How do they interact with each other? What are they actually doing? Is the extra code you see custom code or malware?
- Backend tools: Working familiarity with cPanel, SFTP, File Manager, phpMyAdmin, and all the other tools in your web host account.
If, at all, you are unfamiliar with any of the above, we suggest you stop right here and clean using MalCare. We have mentioned before that time is of the essence, and this is not the moment to gain proficiency in these tools in order to deal with a hack.
a. Get access to your website
If your web host has suspended your account, then this is the first step. Otherwise, skip to the next one.
Contact web host support to get them to whitelist your IP for cleaning. They would have blocked your website after running scans, so ask for those results as well. The results will provide a starting point for cleaning up the malware.
b. Take a backup of your website
This is a critical step in the cleanup: please take a backup of your website. Manual cleanups can go sideways very quickly, and a backup is the only thing that will save the day. Even a website with malware on it is better than no site whatsoever.
If your web host detects malware on your website, they could also delete it without warning. Of course, this depends on the web host in question, but it is really better to err on the side of caution.
To take a backup, use BlogVault. There is a 7-day free trial to get you started, and once set up, it will take regular automated backups of your website. Even if your web host takes down your website, you will still have your web site backups, because BlogVault backups are stored on external servers. Plus, a backup plugin is always a much better bet than relying on manual backups and restores.
c. Download WordPress core, plugins and themes again from the repository
We don’t know where malware could be hiding, so luckily there are some things you can replace entirely without a problem. Make a note of the versions that were installed on your website, and download those. Older or newer versions may have different code, and may cause compatibility issues on your website later.
Once downloaded and unzipped, compare the files and folders of the fresh installs with those on your website. This is a tedious process to do manually, so you can use an online diffchecker to highlight the differences. It will still be tedious, but somewhat faster.
A word of caution here: custom code from your website is not malware. It is sometimes necessary for web designers to alter official code to create the right experience for the website. The differences may be due to this reason.
As an aside, this file-matching technique is what most security plugins, except MalCare, use to discover malware. It can prove to be ineffective, especially in the case of custom code.
In any case, make notes of all the differences, and set the files aside. At this point, don’t delete anything.
d. Check for fake plugins
Since you have a list of plugins and themes easily at hand now, you can check if any of them are fake plugins. You will not find fake plugins in the WordPress repository to download, and the plugin folder will typically contain very few files, sometimes just the one file. Fake plugins also don’t follow the typical naming conventions for WordPress plugins.
If you are using nulled software at all, you can rest assured that this is probably the reason your website got hacked in the first place. Nulled plugins and themes are attractive for their low prices, but come at a high cost. Hackers infuse the code with malware or backdoors at the very least, and wait for people to install them, thus rolling out a welcome mat for their nefarious activities.
e. Reinstall WordPress core
Now that you have the fresh installs, it is time to start replacing files and folders. The reason we suggest doing it this way is because fresh installs will take care of the malware loaded in the file directory of your website.
However, this method is not without its risks too. An install or restore can fail just as well, so please backup your website in case you haven’t already done so.
Log into the cPanel of your web hosting account, and use the File Manager tool to access your website files. Replace the following folders entirely:
Fortunately, these 2 folders contain core WordPress files only, and rarely change even between versions. Your content and configurations are stored elsewhere, so they will remain unaffected. In fact, these folders should not differ from their clean installation counterparts.
Next, look for odd code in these critical files:
- index.php
- wp-config.php
- wp-settings.php
- wp-load.php
- .htaccess
We realise that ‘odd code’ is not an easy directive to follow, but malware can take many forms. We suggest looking for scripts that aren’t present in the clean installations, and scrutinising those carefully. Just because they aren’t there in the clean installs doesn’t make them malware, but it is a good place as any to start.
Please be extremely careful if you choose to poke around in these files. One small change can bring down your website altogether. Retrieving after that is a tough task.
Next, the /wp-uploads shouldn’t have any PHP files (files like wp-tmp.php) at all. Delete any that you find in that folder.
Unfortunately, we cannot give more specific advice at this juncture. As we said before, malware can look like absolutely anything. We’ve seen hacked image files and icon files, all of which look entirely innocuous at first glance.
If you think an entire file is malware, quarantine the file instead of deleting it. That means, you change the file extension to something that isn’t executable: like php to pho for example.
If you suspect some code is malicious, then try deleting it to see what happens. In case your website breaks, you can replace the file with the same one from your backup.
f. Clean plugin and theme folders
Next up for cleaning is the /wp-content folder with all the plugin and theme files. Repeat the same process you just did with the core WordPress files, comparing the code carefully to find changes and additions.
Again, we want to caution you against deleting anything different summarily. If you have changed settings and configurations, you should expect to see some changes in the code. However, if you are comfortable with wiping out customization entirely, then the fastest way to clean up the malware hiding in these files is to replace the plugins and themes files entirely.
In our experience, admins are unwilling to lose any customization, and that’s a fair stance to take because of the work involved.
While cleaning out malware, it is helpful to know how the code functions on the website. Malware scripts can be entirely harmless, until another file executes them. The second file will also look completely harmless as well. This lock-and-key mechanism of some malware also makes it difficult to spot.
If your website has a lot of plugins and themes, active or otherwise, this step can take a team of searchers several days to go through. In the interest of time, check for malware in the following files of the active theme:
- header.php
- footer.php
- functions.php
In a previous section, we mentioned looking for vulnerabilities in your installed plugins. Start with those plugins, and work through the list. Don’t stop looking, even if you think you have found the malware halfway through your list. Malware can exist in all files simultaneously, so you have to check everything.
g. Clean malware from database
Get a download of your website database, either from phpMyAdmin or from the backup you took. Check each of the tables for unexpected scripts. Start with posts and pages, as these are the most typically targeted and work from there.
In the case of the redirect hack, the malware infects every single post and page. So if you find the malware script in one, you can use SQL queries to find the same script in the other posts and pages and clean it out. Our earlier caveat still applies though: don’t stop looking halfway through.
You need to take special care if yours is an e-commerce website. Your database will contain critical user and order information, so please be 100% certain you are only deleting malware.
h. Remove all backdoors
Once you’ve gotten the infection out, it is time to close up the entry point. Those may be vulnerabilities in plugins and themes, which you need to address later by updating them. However, before that, you need to check for backdoors.
Backdoors are the secret tunnels into your website, and if they remain that your website is sure to get infected again. Unfortunately, just like malware, a backdoor can be just about anywhere.
Try looking for functions like these:
- eval
- base64_decode
- gzinflate
- preg_replace
- str_rot13
This code doesn’t mean that they are backdoors, because there are legitimate uses for this code. But it could be, so it is worth checking out. Before deleting them though, analyse them thoroughly to ascertain what they do.
i. Reupload your cleaned files
Once you’ve got a clean website, you have to restore it. First, you need to delete the existing files and database, and upload the cleaned counterparts instead. Log into cPanel and use the File Manager and phpMyAdmin to do this. Alternatively, you can use SFTP to manage the restoration process.
j. Clear the cache
Empty WordPress cache, so that your visitors’ browsers load up the cleaned version of your website, not the old hacked version.
k. Use a security scanner to confirm that the malware is definitely gone
This is basically a check to see everything has gone as planned, and that you have indeed cleaned out the malware successfully. Use the same scanner from the scanning section to confirm.
Why you should avoid manually cleaning a hacked WordPress site?
A hack is like an infection, and you would have seen us refer to malware in those terms throughout the article. If you had an infection, you would want to go to a specialist for removal. You wouldn’t try to find each instance of the infection in your system, and remove it one by one.
This may sound dramatic, but a website is critical for those who run them. They can be the cornerstone of your business, and shouldn’t be taken lightly. Even personal blogs account for time invested.
Manual cleanups often go awry, and entire websites are lost. Bringing them back after that is difficult, unless you have a backup to begin with. That’s why we stressed on backups so strongly in the beginning.
Even WordPress security experts use tools to find malware, because it is just better to do so. A security plugin is a tool that you can use minus the expert to free your website from the clutches of malware.
Remove Deceptive Site Ahead by Submitting Review Request to Google
At this point, the Deceptive Site Ahead warning will still be there, even though the malware has been removed. This is because Google hasn’t scanned your newly cleaned website yet. They eventually will, but there is no way to tell how long that will take, so you need to take steps to get past deceptive site ahead.
WARNING: Before you submit a review request with Google, you need to be 100% certain that your website has no traces of malware present anywhere on it. If your website is still infected, Google will reject your request to fix the deceptive site ahead warning message from your WordPress site. Get rejected by Google too many times and Google will flag you as a ‘Repeat Offender’ and you won’t be able to request a review for 30 days.
Requesting a review is a simple process, and each of the requests is manually reviewed by their team.
- Log into Google Search Console
- Find the Security Issues tab, and scroll down to the bottom
- Click on the ‘Request a review’ button
.png)
- Fill in the form with all the relevant information of the steps taken to resolve the security issues
.png)
The review request takes a few days to be resolved, and unfortunately, throughout that time, the Chrome Deceptive Site Ahead warning will stay put. This can’t be helped nor speeded up. It is bad practice to send too many review requests to Google as well, and that strategy will backfire if they block you as a repeat offender.
The key here is to be patient, and await the request results.
What if your site is clean and the review request still fails?
We have often had people email us with this issue, saying that their clean website is being flagged for deceptive content. This is usually caused by two situations:
- If the admin used another plugin to clean their website, or tried to do it manually, some malware was left behind. So the clean up was a failure, and Google detected it as such.
- If the clean up was a success, there may be small remnants like bad links that are causing the alerts.
- Google Safe Browsing rarely shows false positives, but if they do it is because their tools are scanning cached versions of the website. Clear the website cache, and scan once more to be absolutely sure the malware is definitely gone. Then you can request another review.
How to prevent the Deceptive Site Ahead error message from reappearing?
Protect your website from malware, and your website should never have another case of the deceptive site ahead message. It may sound simple, but protecting your website amidst an ever-evolving threat landscape, without help, is no joke.
Here are steps you can take to prevent reinfection, and protect your website, data and visitors from harm:
- Install a security plugin like MalCare, an all-in-one solution that scans, cleans and protects your website
- Implement strong password policies, like requiring regular changes
- Review user accounts regularly, and only grant minimum privileges required
- Choose good plugins and themes from reputed developers; definitely no nulled software
- Install SSL to encrypt communication back and from your website
- Update everything regularly, especially updates that patch security vulnerabilities
- Invest in backups for insurance
- Implement WordPress hardening measures that work in a few quick clicks.
Website security is an ongoing process, because malware keeps changing. A good security plugin is a non-negotiable part of a good security strategy and will stand you in good stead in the long run.
Why does Google flag dangerous sites?
Google Safe Browsing is a feature that Google provides their search users, so that they can have a safe browsing experience (as the name suggests). Therefore Google wants to keep their users away from deceptive content, spam content, malicious code, and dangerous sites.
An example of dangerous browsing experience is when hackers can insert deceptive content into a website to trick visitors into sharing sensitive information, like passwords or credit card details. This is known as phishing, and is a type of social engineering attack.

Google Safe Browsing also protects users from visiting sites with harmful downloads. A hacker can also use your website to infect many user devices, if they download that content.
Hackers and malware are a dangerous menace, and plenty of people and businesses have sustained losses because of their nefarious activities. Google, and many other responsible companies, want to protect users on the Internet, and Safe Browsing is a way to do that.
What causes the Google Chrome Deceptive Site Ahead to appear on a website?
Malware-infected websites are used to spread viruses, keyloggers, and trojans to other devices. They can also be used to facilitate other hacks and malicious attacks. Ultimately, they are used to steal critical data, like login credentials and financial information.
These are some of the typical infections we have seen that trigger the deceptive site ahead warning:
- Phishing is a social engineering attack, which means the hacker has set up a seemingly official webpage to hoodwink a user into willingly giving up their information like their credit card numbers, phone number and email. This is the biggest reason a website is flagged as deceptive, even though Google Safe Browsing has a warning dedicated to flagging phishing websites.
- Embedded social engineering content can promote malicious links and illicit business. They can also redirect your web users to a malicious website. Quite often, this embedded content is hidden from administrators, so only visitors see them.
- WordPress XSS attacks can exploit vulnerabilities in your website, plugins and themes to insert malicious JavaScript into your frontend or backend code.
- SQL injection attacks can be used to infiltrate, modify, and destroy a website’s database. It can also be used to send a copy of the entire database to the hacker.
- Incorrect installation of your SSL certificate can sometimes cause the warning to be shown, because your website now effectively has content showing up from 2 separate websites: the HTTPS one and the HTTP one. This is more commonly known as the mixed content warning, as Google treats HTTP and HTTPS websites as separate entities.
In addition to malware infections, Google will also flag your website if you have “insufficiently labeled third-party services”. What this means is that if you are operating a website on behalf of some other entity but you have not indicated that clearly on your website, your content can be considered deceptive.
Article: Source







.png)
.png)




